It’s time to ditch cloud based password managers. There.. I said it. What we are doing when we use them is giving ownership and management of our trusted secrets to someone else, and hoping that they will be able to protect them from bad guys, and make sure they are available when we need them.
That’s a heck of an ask, isn’t it? I’ve been a LastPass customer for a very, very long time.. I use it to share secrets with my family, I use it on my mobile device to log into apps. It’s a safe bet to say it’s a critical piece of how I operate, and they have never once let me down. That said, if they asked for money to continue using their service, I’d have to pay. If they had a security event where secrets were compromised or if they lost my data, I’d be in very, very bad shape.
In this article, I will talk about how to set up a WebDAV share that’s protected by HTTPS using Traefik, Let’s Encrypt, and a WebDAV container on your own server, and use it to sync your secrets with devices.
Before I begin, it’s important to understand that using WebDAV isn’t the only way to sync your secrets with Enpass. There are others:
- Dropbox
- Google Drive
- OneDrive (Personal/Business)
- iCloud
- Box
- Folder sync
Table of Contents
Base Server Set Up
Get a VPS
First thing we need is a server that is public internet facing. The easiest way to do this is to use a service that provides virtual private servers. I like Vultr because of their price/performance/feature availability ratio. They are cheaper than DigitalOcean and AWS, as easy, if not easier to manage, and have the scale you need to put your data pretty much wherever you want. If you do use Vultr, please do me a favor and use this link to sign up. I’ll get a little kickback, but you’ll get $100 USD to use on the site in your first month.

The OS doesn’t really matter, as long as you can install docker on it. A very small VPS will suffice, and mine costs $3.50 USD/Month.
Harden the OS
I won’t go into very much depth with this subject, but here are a few general guidelines:
- Disable root login via SSH
- Require public key authentication for SSH sessions
- Enable multi factor authentication for your remote user
- Only install packages you need
- Ensure all updates are installed, and continue to do so on a regular basis
Set Up Docker, Traefik, and WebDAV
All code is on the GitHub repository I use to share all code for this site. You can find it here: https://github.com/jonhowe/Virtjunkie.com/tree/master/DitchLastPass
First and foremost, this will not be a tutorial on how to administer Docker, WebDAV, or especially Traefik, but I’ll give you the exact steps and code for setting this up yourself, and provide some links at the end you can use to learn more about these topics.
All of the following steps will be executed on your VPS, so please sure you are connected to it via SSH or a similar terminal window.
We’ll be using an external docker bridge network in this configuration, the following command will create it
|
1 |
docker network create proxy
|
Create Traefik Configuration
First of all, let’s create the directory structure we’ll need for Traefik (line 1). We’ll also be creating a file that will be used for storing SSL certificates (line 2), and setting permissions on it (line 3).
|
1
2
3
|
mkdir -p $HOME/docker/traefik/data
touch $HOME/docker/traefik/data/acme.json
chmod 600 $HOME/docker/traefik/data/acme.json
|
Create Traefik Configuration
Create a new file in the traefik/data directory we just created called traefik.yml with the contents below.
Changes Required:
- Line 24: Modify your email address
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
#File Path
#$HOME/docker/traefik/data/traefik.yml
#http://www.virtjunkie.com/ditch-lastpass-for-enpass-webdav-https-traefik/
#https://github.com/jonhowe/Virtjunkie.com/tree/master/DitchLastPass
api:
dashboard: false
entryPoints:
http:
address: ":80"
https:
address: ":443"
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
certificatesResolvers:
http:
acme:
email: your.email@domain.com
storage: acme.json
httpChallenge:
entryPoint: http
|
Define Traefik Container
Create a new file in the traefik/data directory called docker-compose.yml
Changes Required:
- Line 30: Modify to fit the hostname of your server
- Line 31: Add in credentials compatible with basic auth. You can use the output from the command below to achieve this.
echo $(htpasswd -nb [your user] [your pass]) | sed -e s/\$/\$\$/g
- Line 35: Modify to fit the hostname of your server
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
|
#File Path
#$HOME/docker/traefik/docker-compose.yml
#http://www.virtjunkie.com/ditch-lastpass-for-enpass-webdav-https-traefik/
#https://github.com/jonhowe/Virtjunkie.com/tree/master/DitchLastPass
version: '3'
services:
traefik:
image: traefik:v2.0
container_name: traefik
restart: unless-stopped
security_opt:
- no-new-privileges:true
networks:
- proxy
ports:
- 80:80
- 443:443
volumes:
- /etc/localtime:/etc/localtime:ro
- /var/run/docker.sock:/var/run/docker.sock:ro
- ./data/traefik.yml:/traefik.yml:ro
- ./data/acme.json:/acme.json
- ./data/logs/:/logs/
labels:
- "traefik.enable=true"
- "traefik.http.routers.traefik.entrypoints=http"
- "traefik.http.routers.traefik.rule=Host(`custom.hostname.com`)"
- "traefik.http.middlewares.traefik-auth.basicauth.users=traefikuser:htpasswd-encrypted-string"
- "traefik.http.middlewares.traefik-https-redirect.redirectscheme.scheme=https"
- "traefik.http.routers.traefik.middlewares=traefik-https-redirect"
- "traefik.http.routers.traefik-secure.entrypoints=https"
- "traefik.http.routers.traefik-secure.rule=Host(`custom.hostname.com`)"
- "traefik.http.routers.traefik-secure.middlewares=traefik-auth"
- "traefik.http.routers.traefik-secure.tls=true"
- "traefik.http.routers.traefik-secure.tls.certresolver=http"
- "traefik.http.routers.traefik-secure.service=api@internal"
networks:
proxy:
|
Start Traefik Container
|
1
2
|
cd $HOME/docker/traefik
docker-compose up -d
|
Create WebDAV Configuration
Before we begin, we need to create the directory structure for the WebDAV container. Use the following command to do so.
|
1 |
mkdir -p $HOME/docker/webdav/dav/
|
We’ll be using a container authored by bytemark for this project. It’s essentially just apache with the webdav module installed. As of today, the container is less than 100MB.
Define WebDAV Application Configuration
Changes Required:
- Line 15: Username used to authenticate to the WebDAV service.
- Line 16: Password you’ll use to authenticate to the WebDAV service. This is stored in plaintext in this example, but storing the variable in an external file is best practice.
- Line 17: Modify to fit the hostname of your server
- Line 27: Modify to fit the hostname of your server
- Line 31: Modify to fit the hostname of your server
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
|
#File path
#$HOME/docker/webdav/docker-compose.yml
#http://www.virtjunkie.com/ditch-lastpass-for-enpass-webdav-https-traefik/
#https://github.com/jonhowe/Virtjunkie.com/tree/master/DitchLastPass
version: '3'
services:
webdav:
image: bytemark/webdav
container_name: webdav
restart: unless-stopped
environment:
AUTH_TYPE: Basic
USERNAME: your-username
PASSWORD: secure-passsword
SERVER_NAMES: your-dav.domain.com
networks:
- proxy
security_opt:
- no-new-privileges:true
volumes:
- ./dav:/var/lib/dav
labels:
- "traefik.enable=true"
- "traefik.http.routers.webdav.entrypoints=http"
- "traefik.http.routers.webdav.rule=Host(`your-dav.domain.com`)"
- "traefik.http.middlewares.webdav-https-redirect.redirectscheme.scheme=https"
- "traefik.http.routers.webdav.middlewares=webdav-https-redirect"
- "traefik.http.routers.webdav-secure.entrypoints=https"
- "traefik.http.routers.webdav-secure.rule=Host(`your-dav.domain.com`)"
- "traefik.http.routers.webdav-secure.tls=true"
- "traefik.http.routers.webdav-secure.tls.certresolver=http"
- "traefik.http.routers.webdav-secure.service=webdav"
- "traefik.http.services.webdav.loadbalancer.server.port=80"
- "traefik.docker.network=proxy"
networks:
proxy:
external: true
|
Start the WebDAV Container
Run the following command to bring up the webdav container
|
1
2
|
cd $HOME/docker/webdav
docker-compose up -d
|
Bringing it all together
Summary
At this point you should have two containers running on your VPS. Traefik is acting as a reverse proxy for the WebDAV container, and is providing SSL encryption to it. The SSL certificate is provided by Let’s Encrypt.
Final Directory Structure
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
user@webdav-server:~/docker$ tree
.
├── traefik
│ ├── data
│ │ ├── acme.json
│ │ └── traefik.yml
│ └── docker-compose.yml
└── webdav
├── dav
│ ├── data
│ │ └── Enpass
│ │ └── vault.enpassdbsync
│ ├── DavLock
│ ├── DavLock.dir
│ └── DavLock.pag
└── docker-compose.yml
6 directories, 8 files
|
Migrate to Enpass Using WebDAV
Now that we’ve got a functional and secure WebDAV instance, we just need to migrate to it. These steps are pretty easy, but I want to include them to be comprehensive.
Export Secrets From Lastpass
To make our transition from Lastpass as seamless as possible, we’ll export our secrets so we can import them into Enpass. The easiest way to do this is from the Lastpass Vault.
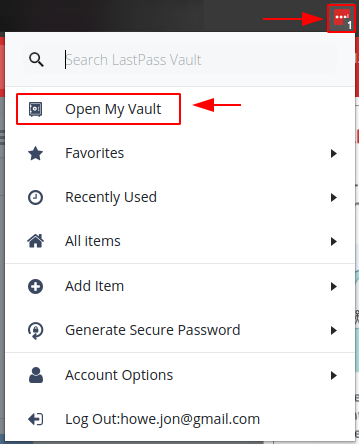
Step 1 – Open Your Vault
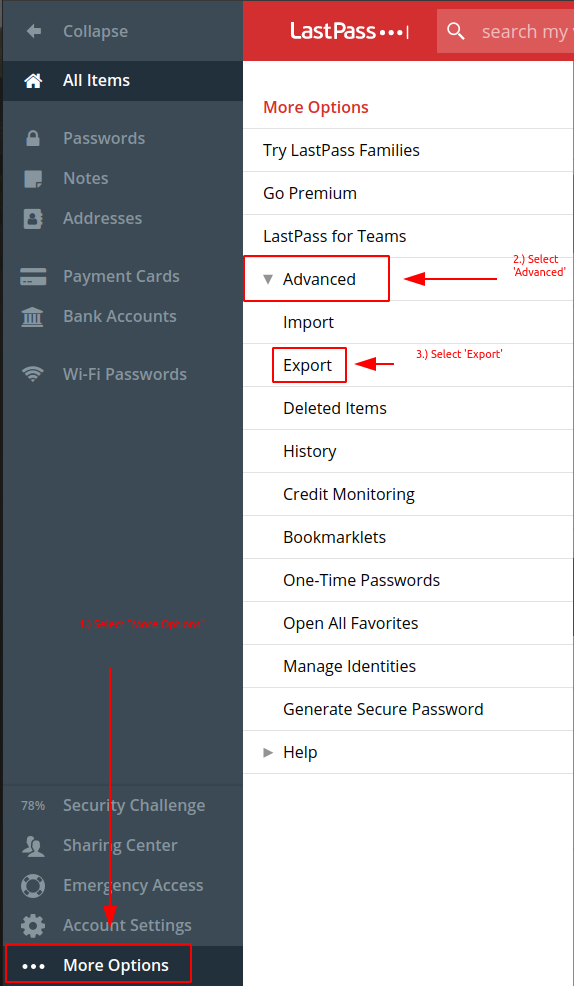
Step 2 – Export Secrets
- Select “More Options”
- Select “Advanced”
- Select “Export”
- If prompted, enter your Master Password, and note where the CSV export file name and path.
Import Secrets To Enpass
Pretty easy stuff here, just open enpass, and kick off the import.
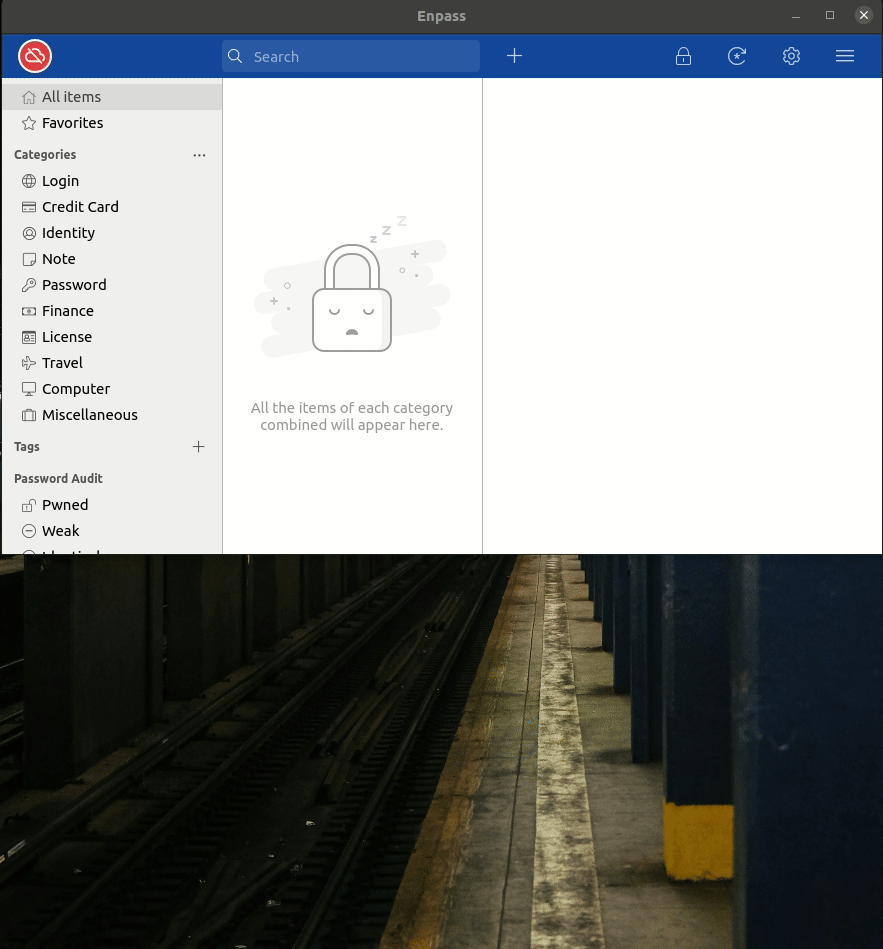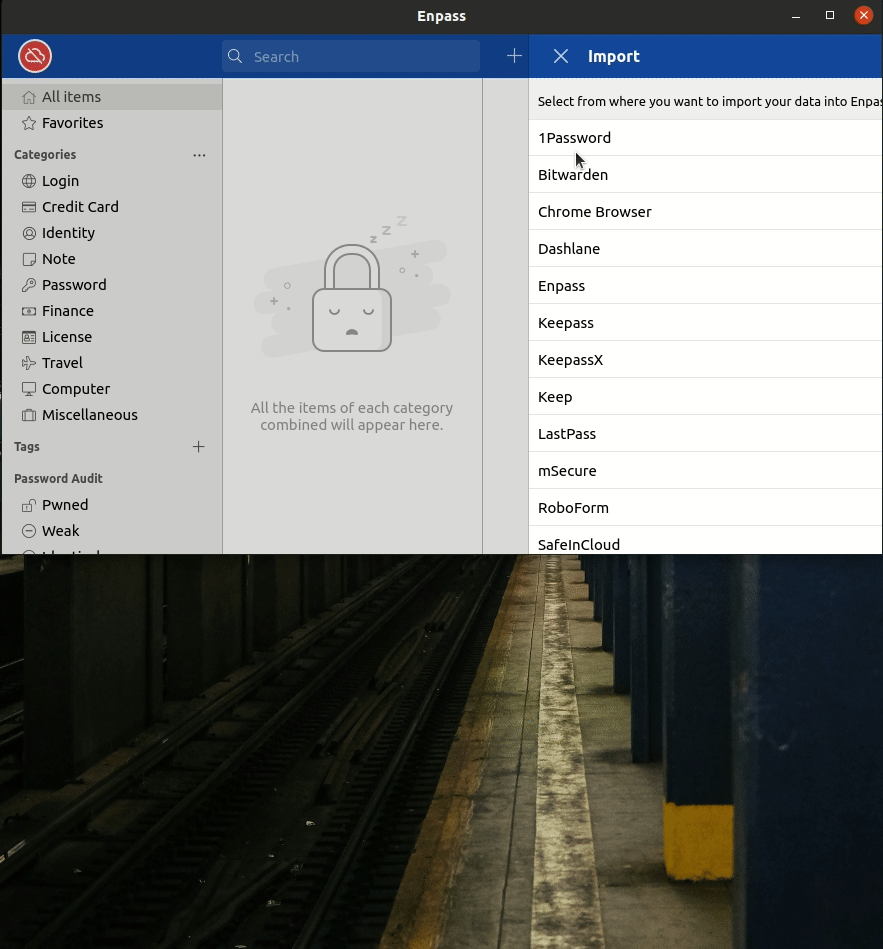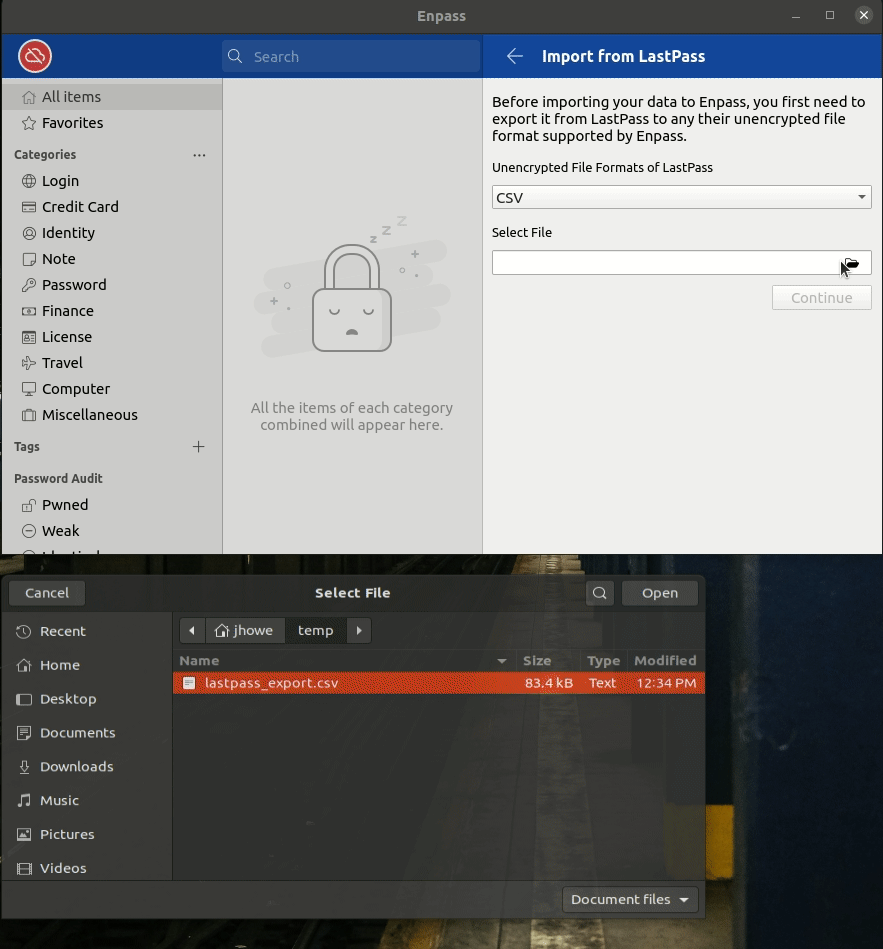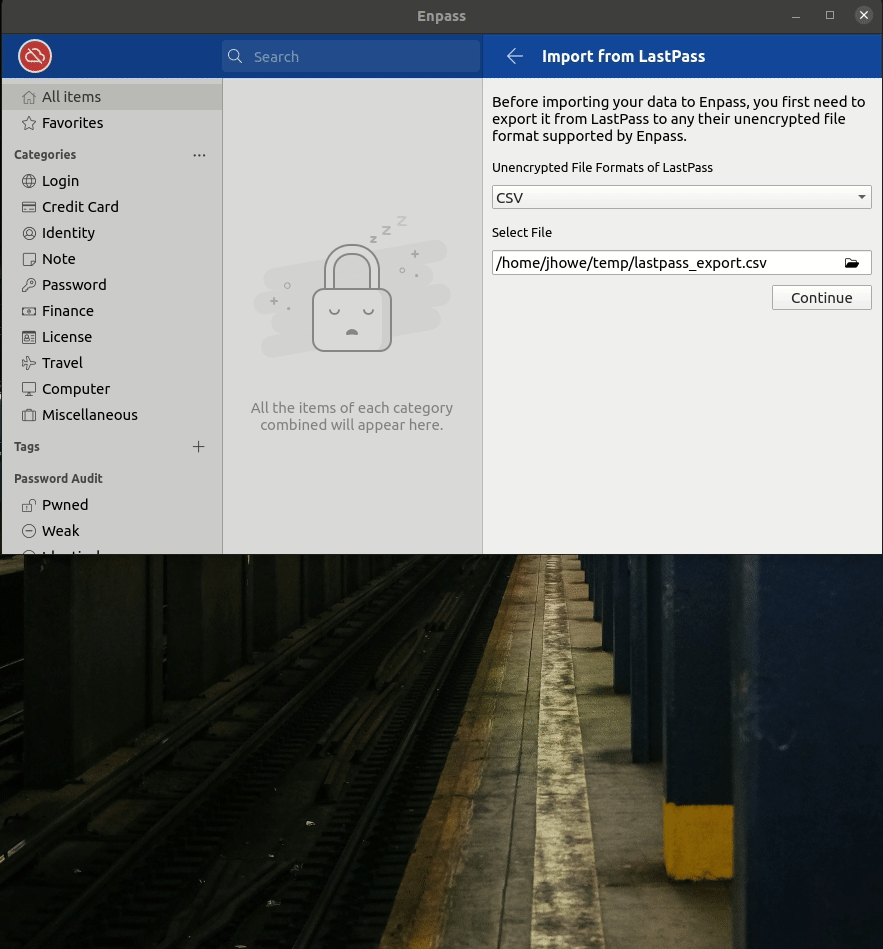
Import Steps:
- Open Enpass
- Select Menu
- Select File
- Select Import
- When prompted to “Select from where you want to import your data into Enpass”, select Lastpass
- Navigate to the directory you exported the CSV to
- Select continue to finish the import
Connect EnPass To WebDav Share
At this point you’ve got a functioning WebDAV service protected by SSL, as well as a local instance of Enpass that has your lastpass secrets. We just need to connect EnPass to your Webdav instance to allow us to sync to it. Once you have EnPass Installed, follow the steps below to connect it to your WebDAV Service.
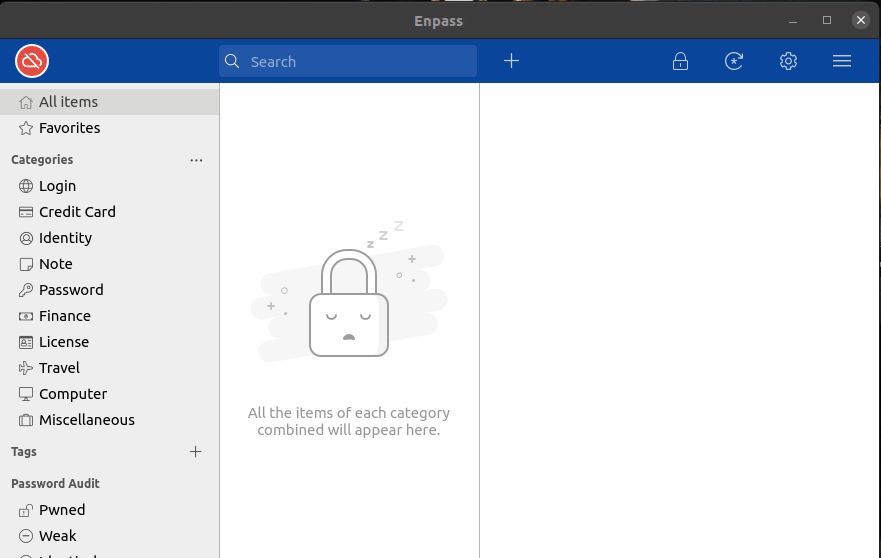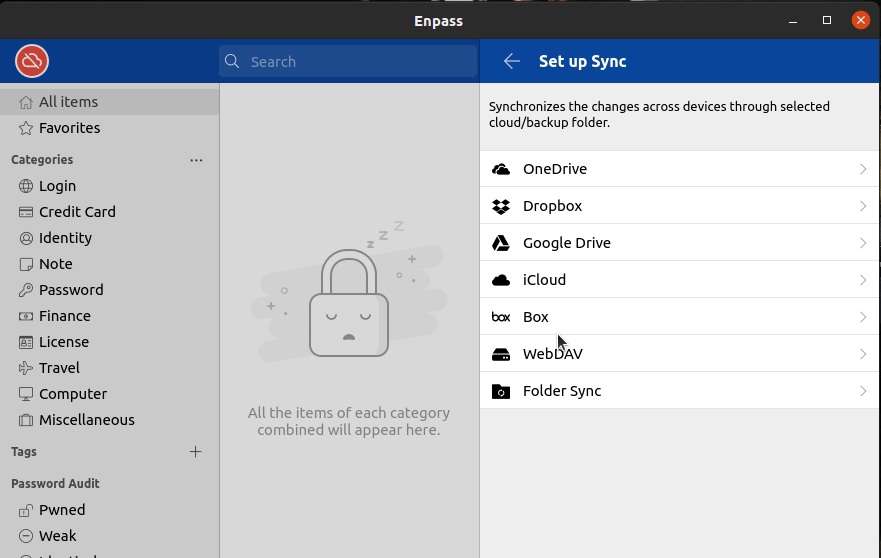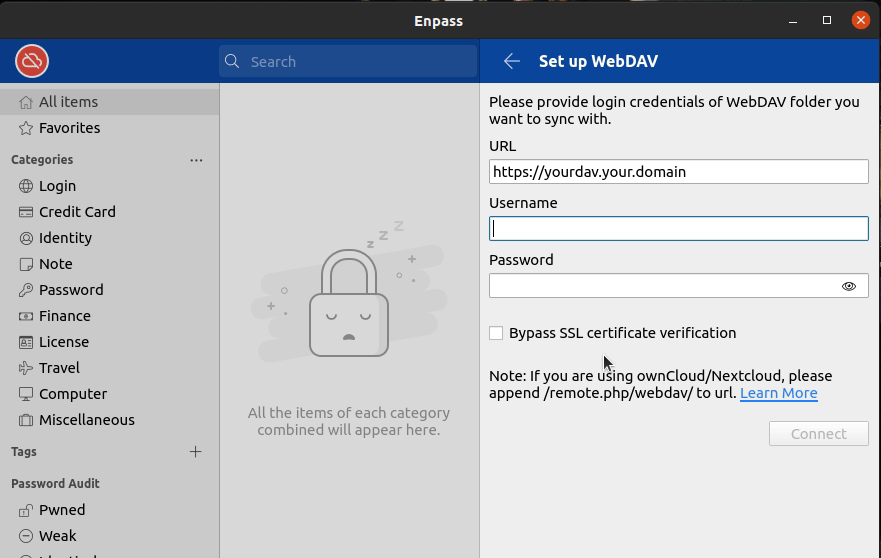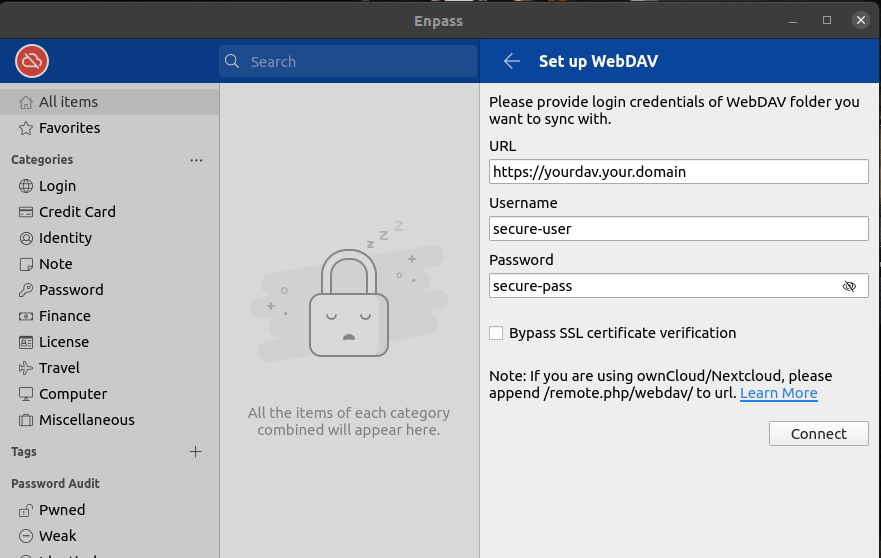
Connection Steps:
- Open Enpass
- Select Settings
- Select Vaults
- Select the Vault you’d like to sync
- Enter the URL of your server, and ensure to include the https:// prefix
- Enter the username and password created in Section 2.2.1
- Ensure that the checkbox for “Bypass SSL Certificate Validation” is unchecked. We want to validate the SSL certificate since we are using Let’s Encrypt.
Risks
There are some things that LastPass does for us that we don’t get with this solution. In particular, we are somewhat exposed to brute force attempts to the webdav service. Also, LastPass has a number of email notifications that go out when things happen in your vault. We are really only notified when a new client joins the vault in Enpass.
Trafeik Resources
https://medium.com/@containeroo/traefik-2-0-docker-a-simple-step-by-step-guide-e0be0c17cfa5
https://containo.us/blog/traefik-2-0-docker-101-fc2893944b9d/